READ Free Dumps For Microsoft- 70-411
| Question ID 14077 | Your network contains one Active Directory forest named contoso.com. The forest contains
a single domain. All domain controllers are virtual machines that run windows server 2012
R2. The functional level of the domain and the forest is Windows Server 2012 R2.
The forest contains the domain controllers configured as shown in the following table.

In the table below, select the domain controller that can be cloned by using domain
controller clonning and select the domain controller that must be online to perform domain
controller cloning.
Note: Make only one selection in each column.
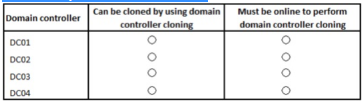
|
| Option A | 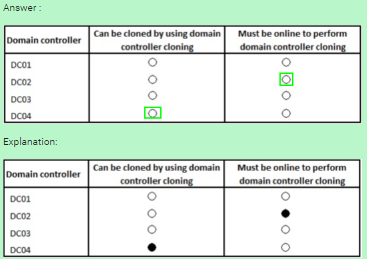
C:\Users\Kamran\Desktop\sample.jpg PDC Emulator must be online to perform Domain Controller Cloning. The following server roles are not supported for cloning: Dynamic Host Configuration Protocol (DHCP) Active Directory Certificate Services (AD CS) Active Directory Lightweight Directory Services (AD LDS) https://technet.microsoft.com/en-us/library/hh831734.aspx#virtualized_dc_cloning http://blogs.technet.com/b/canitpro/archive/2013/06/12/step-by-step-domain-controller- cloning.aspx
|
| Correct Answer | A |
Explanation
| Question ID 14078 | Your network contains an Active Directory domain named contoso.com. The domain
contains a server named Server1 that runs Windows Server 2012 P.2. Server1 has the
Network Policy and Access Services server role installed.
Your company's security policy requires that certificate-based authentication must be used
by some network services.
You need to identify which Network Policy Server (NPS) authentication methods comply
with the security policy.
Which two authentication methods should you identify? (Each correct answer presents part
of the solution. Choose two.)
|
| Option A | MS-CHAP
|
| Option B | PEAP-MS-CHAP v2
|
| Option C | Chap
|
| Option D | EAP-TLS
|
| Option E | MS-CHAP v2
|
| Correct Answer | B,D |
Explanation Explanation: PEAP is similar in design to EAP-TTLS, requiring only a server-side PKI certificate to create a secure TLS tunnel to protect user authentication, and uses server-side public key certificates to authenticate the server. When you use EAP with a strong EAP type, such as TLS with smart cards or TLS with certificates, both the client and the server use certificates to verify their identities to each other.